Explain
the ethical issues surrounding information technology
Ethics is a system of moral principle that
considers our actions from right and wrong. Ethical issues surrounding informational
technology consist of the following
-Intellectual property: collection of rights that protect creative and intellectual
effort.
-Copyright:
Exclusive right to do certain acts with intangible property
-Fair use
doctrine:
In certain situations, it is legal to use copyrighted material
-Pirated
software:
unauthorized use, duplicate, distribution, or sale of copyrighted software.
-Counterfeit
software: software that is manufactured to look like the real thing and sold as
such
Describe a
situation involving technology that is ethical but illegal
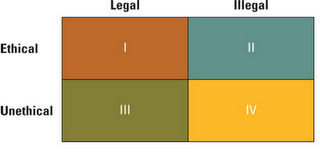 A situation involving technology that is ethical but
illegal may be; when one purchases a program for their computer and creates a backup
copy in case of any damage or loss of the original. Even though it states that
copies of the program are illegal and should not be made the backing up of a program
for your own use is not cheating the procedures of customers. This situation is
most definitely considered unethical if the copy is being made multiple times
to sell over the internet or at a market then the issue becomes both unethical
an illegal.
A situation involving technology that is ethical but
illegal may be; when one purchases a program for their computer and creates a backup
copy in case of any damage or loss of the original. Even though it states that
copies of the program are illegal and should not be made the backing up of a program
for your own use is not cheating the procedures of customers. This situation is
most definitely considered unethical if the copy is being made multiple times
to sell over the internet or at a market then the issue becomes both unethical
an illegal.
Describe and explain one of the
computer use policies that a company might employ
A company may employ an ‘internet use policy’ to contain
general principles to guide the proper use of the internet. This has some
unique aspects that make it a good candidate for its own policy. Implementing
this policy means that all employees are encouraged to use the internet
responsibly. These policies include:
1. Describe available internet services
2. Define the purpose and restriction of Internet access
3. Complements the ethical computer use policy
4. Describes user responsibilities
5. States the ramification for violations
1. Describe available internet services
2. Define the purpose and restriction of Internet access
3. Complements the ethical computer use policy
4. Describes user responsibilities
5. States the ramification for violations
What are the 5 main technology
security risks?
1) Human Error: after complete recheck to find any mistakes
2) Natural Disasters: regularly save data as back up and in alternative
area
3) Technical Failures: install a trustworthy spyware fighter and regularly
save data in a separate
4) Deliberate Acts: constantly monitor the employees actions when working
in the firm
5) Management Failure: Ensure proper training and procedures in the
workplace to new employees

Outline one way to reduce risk
One way to reduce risk may include ‘The second line of
defence technology.’ Organisations can deploy numerous technologies to prevent
information security breaches. When determining which types of technologies to
invest in, it helps to understand the three primary information security areas:
1 ) authentication and authorisation
2) Prevention and resistance
3) Detection and response
What is a disaster recovery plan,
what strategies might a firm employ?
A disaster recovery plan examines those situations that
prevent you from carrying on business. Disaster Recovery is a process of
regaining access to computer systems and data after a disaster has taken place.
Careful planning helps your business get back to normal operations as quickly
as possible. A firm might employ the following strategies.
-
location of backup
data: offsite data kept in order
-
Develop information security policies
-
Communicate the information security policies
-
Identify critical information assets and risks
-
Obtain stakeholder support
No comments:
Post a Comment